For companies using Google Workspace for email and scheduling, and Microsoft Teams for meetings and collaboration, it can sometimes feel like switching between two worlds. Thankfully, there’s a simple way to bring these platforms together by integrating Microsoft Teams directly into your Google Calendar.
Here’s how to do it—and why it matters.
Why Integrate Microsoft Teams with Google Calendar?
Integrating Microsoft Teams with Google Workspace Calendar makes scheduling and joining meetings far more seamless. Whether you’re a business owner, admin, or team member, this setup offers several advantages:
- Streamlined Scheduling: Create Microsoft Teams meetings right from Google Calendar without switching apps.
- Simplified Collaboration: Easily invite colleagues and clients who use different systems.
- Unified Workflow: Manage events and video calls all in one familiar interface.
This is especially useful for organisations that use Google Workspace for productivity but rely on Teams for external meetings or cross-department collaboration.
Step-by-Step: Installing the Microsoft Teams Add-On in Google Calendar
To get started, you’ll need a Microsoft 365 work or school account. Here’s how to integrate Teams into Google Calendar:
1. Open Google Calendar
Use a web browser and sign in to your Google Workspace account.
2. Access the Side Panel
On the right-hand side, click the ‘+’ (Get Add-ons) icon. If the panel is hidden, select “Show side panel” at the bottom of your screen.
3. Search for the Add-On
In the Google Workspace Marketplace, search for “Microsoft Teams Meeting”.
4. Install the Add-On
Click on the Microsoft Teams Meeting app and select “Install”. Follow the steps to grant the required permissions.
5. Sign In
After installation, the Teams icon will appear in the side panel. Click it and sign in with your Microsoft work or school account.
💡 Note: If you’re a Google Workspace admin and wish to install this across your organisation, make sure to enable data access in the Admin Console under Apps > Google Workspace Marketplace apps > Microsoft Teams Meeting > Data Access.
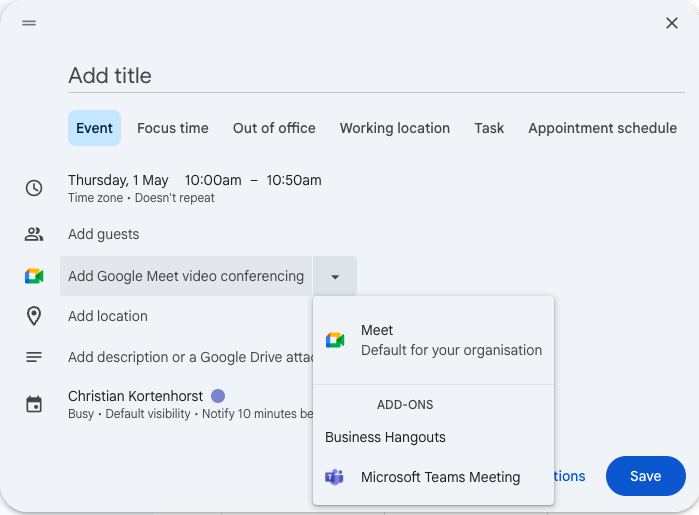
How to Schedule a Teams Meeting from Google Calendar
Once the add-on is installed, creating a meeting is simple:
- Click “Create” in Google Calendar.
- Select “More options” at the bottom of the event pop-up.
- Click on “Add conferencing” and choose “Microsoft Teams meeting”.
- Add your guests, title, time, and any additional notes.
- Click “Save”—your invite will now include a Teams meeting link.
Guests will receive the calendar invite with a link to join the meeting via Microsoft Teams, even if they don’t use Teams regularly.
Troubleshooting Common Issues
If you experience issues, such as an “Authorise Access” prompt:
- Click the link in the add-on panel or event to re-authorise.
- Ensure permissions are correctly set if you’re an admin.
- Refer to Microsoft’s official help article here: Join from Google
- Google Marketplace link https://workspace.google.com/marketplace/app/microsoft_teams_meeting/961264221134?flow_type=2
Integrating Microsoft Teams with your Google Calendar is a small change that can make a big impact on productivity and communication. Especially for Irish businesses using a hybrid approach to technology, this integration brings the best of both platforms together.
You can install the Microsoft Teams Meeting add-on directly from the Google Workspace Marketplace today and start scheduling smarter.