
Jan 14, 2026
Why Every Business Must Protect Its Email Domain with DMARC, DKIM and SPF
Email remains one of the most important tools in any business. It is how invoices are sent, projects are discussed, suppliers are contacted and customers are supported. Because of that…

Dec 18, 2025
How to mind my mac address Windows/Mac/PC/Android/IPhone
Here are clear, step-by-step ways to find the MAC address on the most common devices. The MAC address is usually shown as six pairs of letters and numbers (for example:…
Dec 11, 2025
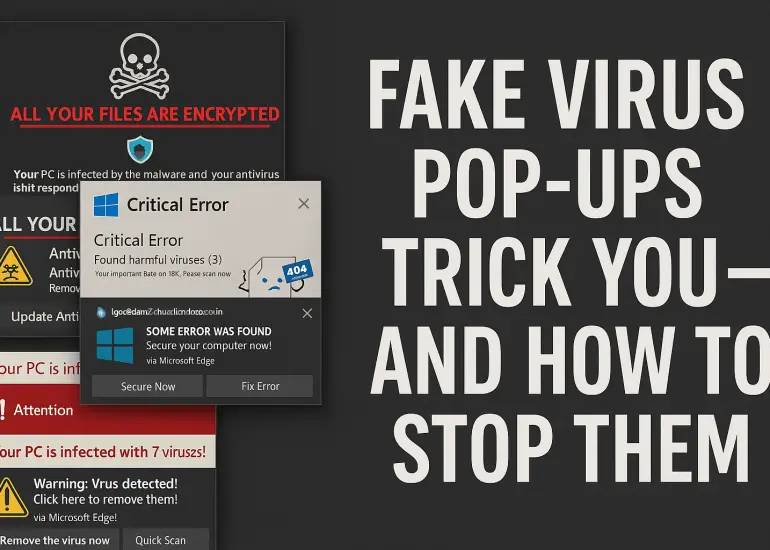
How Fake Virus Pop-Ups Trick You — And How to Stop Them
Those screenshots show classic fake virus alert pop-ups—they’re designed to frighten you into clicking a button, downloading something, or handing over remote access or payment. These aren’t real system messages…
Dec 03, 2025
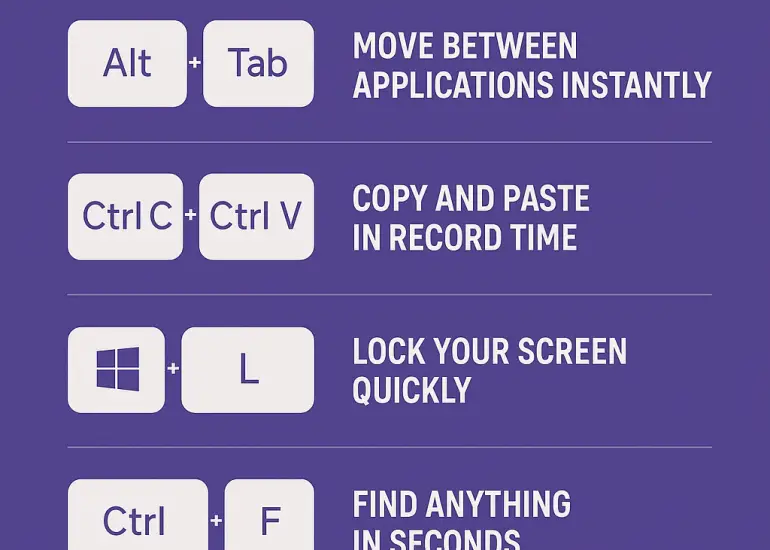
5 Keyboard Shortcuts That Will Save You Hours Every Week
If you spend most of your day at a computer, you’ll know how even the smallest slowdown can throw off your flow. Moving your hand from your keyboard to your…
Oct 08, 2025
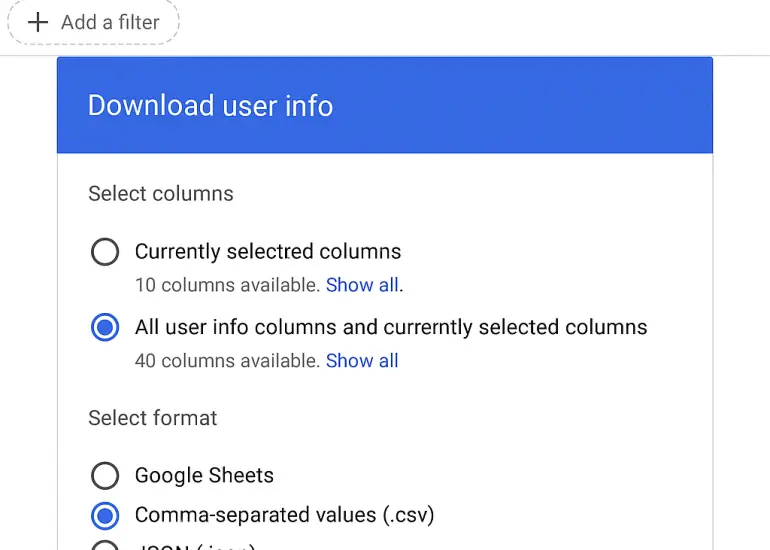
How to Export a List of Users from Google Workspace Admin Console
Keeping track of users in your Google Workspace is essential for managing licences, maintaining security, and ensuring your organisation’s data stays organised. Whether you’re preparing for an internal audit, updating…
Sep 24, 2025
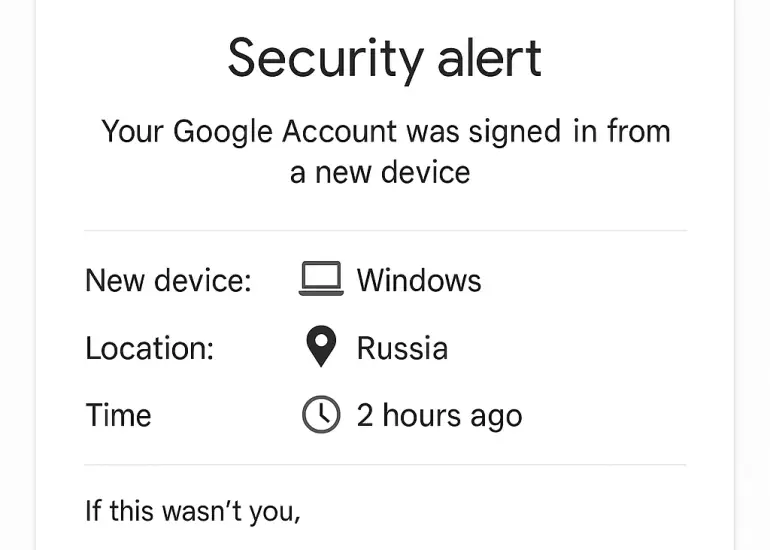
What to Do if Your Google Workspace Account Has Been Hacked
When your Google Workspace account is compromised, the impact can be devastating — from leaked company data to loss of trust with clients. Cybercriminals don’t just stop at your email…

Sep 18, 2025
The Hidden Dangers of Outdated Third-Party Software
Why Third-Party Apps Are a Double-Edged Sword Most businesses rely on third-party applications every day—whether it’s a CRM system, accounting software, file sharing platform, or communication tool. These apps boost…
Sep 10, 2025
SVG Phishing Attacks: The Hidden Cyber Threat Targeting Your Business
1. What is an SVG and why do attackers love it? Scalable Vector Graphics (SVG) is a web image format based on XML. Unlike PNG or JPG, SVG files are…

Sep 09, 2025
How to Upgrade to Windows 11 from Windows 10: A Step-by-Step Guide for Businesses
Microsoft has officially announced that Windows 10 will reach its end of life in October 2025, meaning no more security updates, bug fixes, or official support. If your business or…
