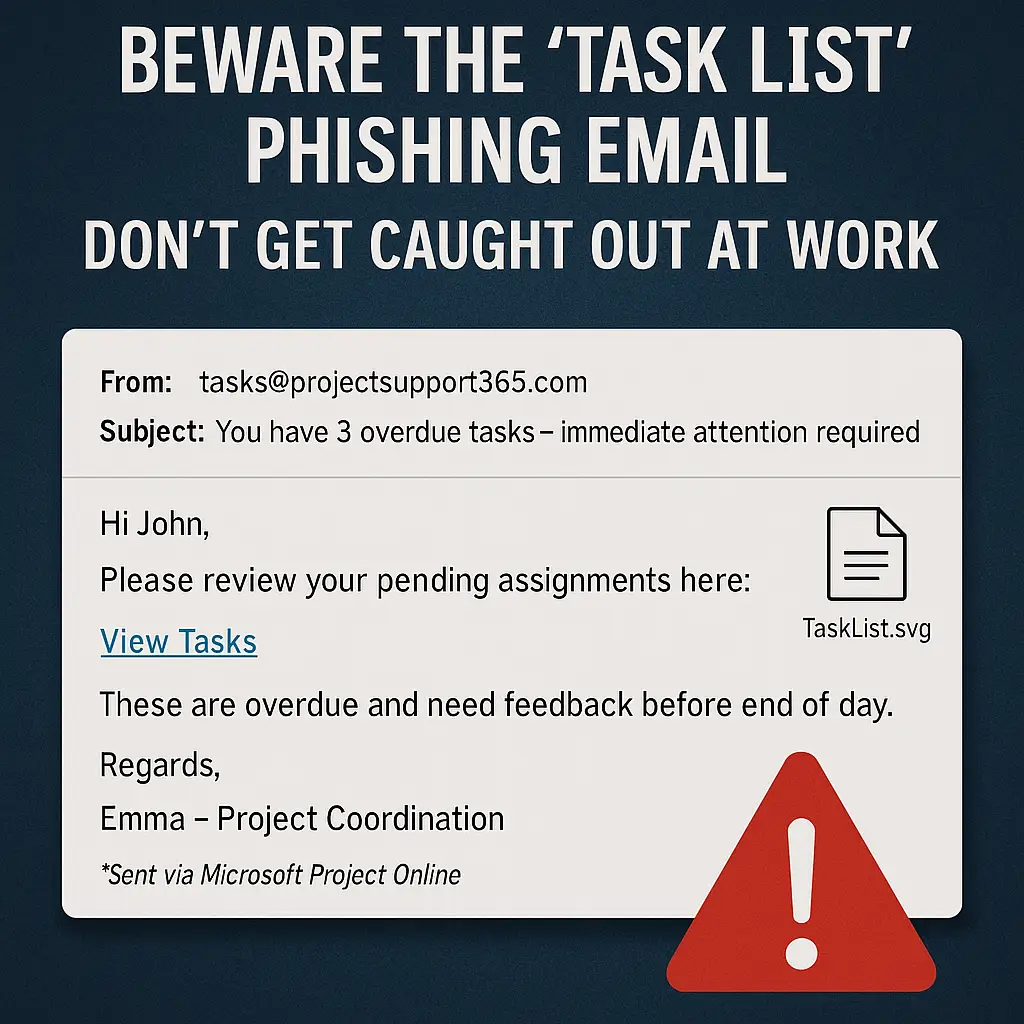
We’ve all had that moment — the mobile rings from a strange number, or a text pops up claiming to be from your bank. You pause, hesitate, and then the sinking feeling hits. “Is this legit… or a scam?”
Well, thankfully, the powers-that-be are doing something about it.
Ireland’s communications regulator, ComReg, has introduced a new “Likely Scam” warning system for mobile calls. It’s a step in the right direction — and a particularly important one for small and medium-sized businesses across the country who are on the frontlines of phone-based communication.
Let’s break down what’s happening, how it works, and what you can do to stay ahead of the curve.
What Is the “Likely Scam” Warning?
The new system automatically labels suspicious calls with a warning on your mobile screen. So, instead of just seeing an unknown number, you might now see:
📱 “Likely Scam”
This feature helps flag calls that appear to spoof real numbers, use known scam patterns, or exhibit suspicious calling behaviour — the kind we’ve seen rise sharply over the past few years.
It’s not blocking the call, just giving you a heads-up. You can still answer if you choose — but now with a much clearer idea of what might be waiting on the other end.
How Does the Scam Alert System Work?
The warning system is built into the mobile network layer. Here’s a simplified overview:
- Telecom providers monitor traffic patterns – These include high-volume, short-duration calls, or calls from numbers that look like Irish numbers but originate from abroad.
- Suspicious activity is flagged – If a call matches the behaviour of known scams, the network applies the “Likely Scam” label before the call reaches your device.
- The label appears on your screen – Just like “Private Number” or “No Caller ID,” it gives you a warning in advance.
This system has already rolled out across major Irish mobile networks like Vodafone, Three, and eir. No setup is required by the user — it’s all managed at the network level.
Why This Matters for Irish Businesses
If you’re running a business in Ireland — whether you’re in retail, services, trades, or tech — your phones are a lifeline. Scam calls aren’t just annoying; they can be dangerous.
Here’s how they cause real problems:
- Wasted time: Staff lose productivity answering junk calls.
- Data breaches: A well-timed phishing call might trick someone into giving out client or system info.
- Reputation damage: If a scammer spoofs your number and contacts others, it reflects badly on your brand.
- Stress and confusion: Constant spam calls erode trust in phone communication and lower morale.
Now, with the “Likely Scam” system in place, you’ve got another tool in the arsenal to defend your staff and your customers from fraudulent activity.
What You Can Do To Protect Your Team and Clients
While the ComReg update is brilliant, it’s just one piece of the puzzle. There are other steps Irish businesses should take to stay cyber-safe:
1. Educate your staff
Hold regular training sessions on how to spot scam calls, phishing texts, and dodgy emails. A five-minute chat could prevent a five-figure loss.
2. Review call handling procedures
Make sure staff verify unexpected requests, especially ones involving passwords, payment details, or system access.
3. Use secure communications platforms
If your team relies on mobile phones, consider pairing them with secure apps like Microsoft Teams or encrypted VoIP services.
4. Enable call filtering
Some mobile devices and VoIP platforms allow for automatic call blocking or routing unknown numbers to voicemail.
5. Have an IT policy in place
Include clear steps on how to report suspicious calls, texts, or voicemails. Quick action can prevent further risk.
How CK Computer Solutions Can Help
At CK Computer Solutions – Managed IT Services Dublin, we work with businesses across Ireland to secure their communications, devices, and systems.
Our managed services go beyond basic support:
- Call Security: We help configure VoIP and mobile setups with added filtering and spam protection.
- Staff Cybersecurity Training: We deliver tailored training sessions on recognising scam calls and social engineering tactics.
- Incident Response: If a staff member does fall victim to a scam, we help contain the breach, investigate what happened, and patch the gap.
- Policy Development: We work with you to create practical, realistic communication policies that protect both your staff and your reputation.
Think of us as your IT partner — not just a helpdesk, but an embedded part of your team, always watching your back.
Whether you’re a small office or a multi-site operation, CK Computer Solutions can help you stay ahead of emerging scams and tighten your tech defences.