A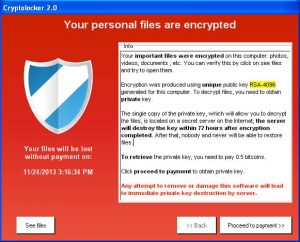 fter being in the technical industry for over thirty years it takes something fairly unique to pique my attention. The Cryptolocker virus is in fact that type of program. In a nutshell it takes all of your files and over a period of days, weeks, and or months turns your most used and precious data into a conglomeration of unusable junk. In conjunction with that the method for recovery from the virus is ingenious at best, and diabolical at worst. The following is the method of transmission, assimilation, and recovering from the Cryptolocker virus.
fter being in the technical industry for over thirty years it takes something fairly unique to pique my attention. The Cryptolocker virus is in fact that type of program. In a nutshell it takes all of your files and over a period of days, weeks, and or months turns your most used and precious data into a conglomeration of unusable junk. In conjunction with that the method for recovery from the virus is ingenious at best, and diabolical at worst. The following is the method of transmission, assimilation, and recovering from the Cryptolocker virus.
Infection
The virus is introduced through an infected attachment in an email. Disguised in the email it immediately propagates the bot and begins its malicious attack on your data. In addition websites can introduce the malware through the use of an advertisement click through that again places the bot on your computer and the process begins.
Virus Process
The virus makes its way through your file system by targeting specific file types in order to achieve maximum damage. Files such as spread sheets, documents, and text files are attacked first and encrypted. If the virus remains undetected then pictures, music, and video are destroyed. The virus starts at older dated files and then continues up the chain until more recently used files are encrypted and then the virus exposes itself.
Remedy
Once your data has been encrypted a covert server will send a message asking for a sum of money to decrypt the data. It is at this time that a mistake is usually made. Most users will run a virus scanner and remove the virus from the computer. This is a grave error as the key to decrypt the data is embedded in the virus executable file. Since the key has been deleted there is no method for decrypting the data including brute force methods. There is only one method for getting your data back and that is to pay the 300 to 400 dollars using the Bitcoin path of money transfer. It is estimated that over 25 million dollars has been extorted from those who have gotten the virus.
In the final analysis, and looking from a strictly objective point of view, Cryptolocker in its delivery method as well as it execution and ultimate payment process offers a well planned and executed criminal enterprise that no one was ever brought to trial for. Many of the servers were finally brought down and that in itself presented a problem for those who caught the virus and tried to pay. There was no server to complete the transaction and therefore the data remained lost.
There is no real method for preventing the payload being delivered to your computer. Only good judgment and making sure that every website, and every email you open is carefully evaluated before proceeding.
