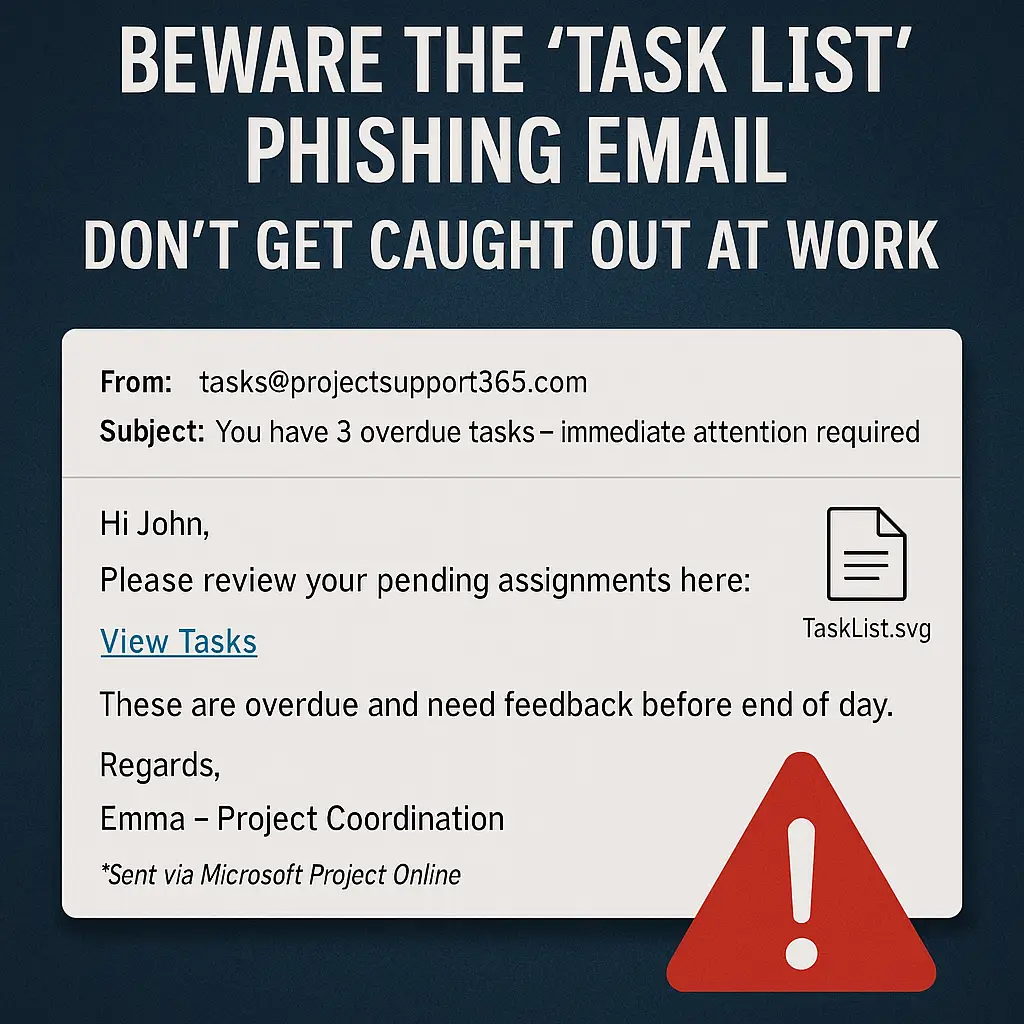
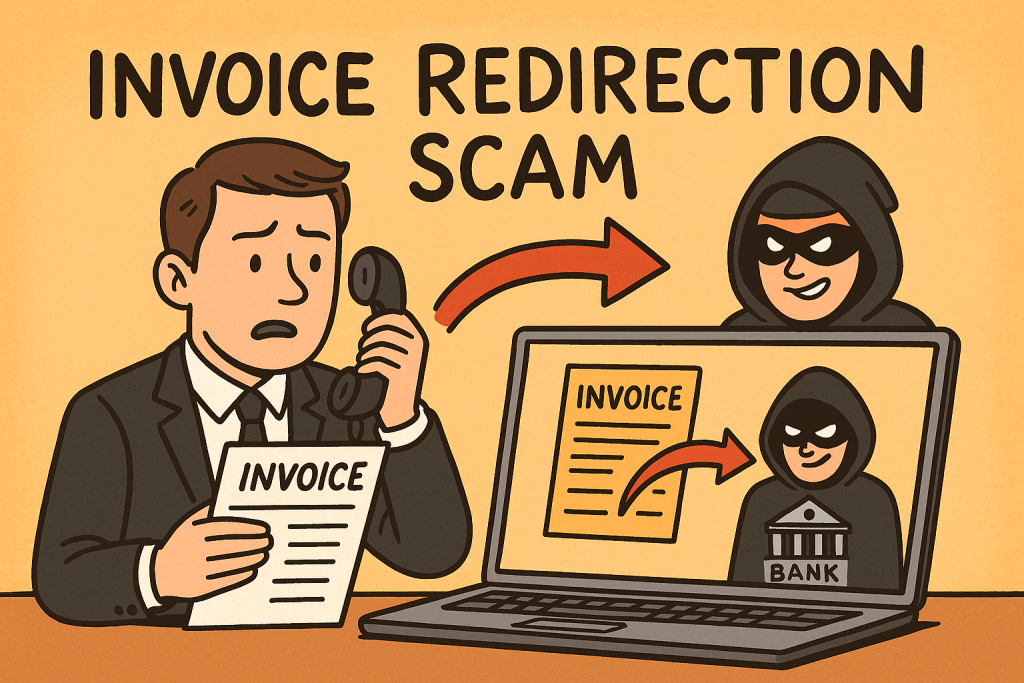
Email remains one of the most important tools in any business. It is how invoices are sent, projects are discussed, suppliers are contacted and customers are supported. Because of that reliance, email is also one of the most abused attack vectors used by cyber criminals.
If your domain is not properly protected, attackers can impersonate your business, send fraudulent emails that look legitimate, and damage both your reputation and your bottom line. This is where DMARC, DKIM and SPF come in. These three technologies work together to protect your domain from spoofing, phishing and email-based fraud.
This article explains what each one does, why they matter, and why no modern business should ignore them.

Why Email Domain Protection Matters
Before diving into the technical side, it is important to understand the risk. When attackers spoof your domain, they are not hacking your email system directly. Instead, they are pretending to be you.
Common real-world examples include:
- Fake invoices sent to customers using your company name
- Fraudulent emails asking staff to change bank details
- Phishing emails sent to customers that appear to come from your domain
- Malware-laced emails that damage trust in your brand
Even if your systems are secure, the damage is still yours. Customers rarely blame “email spoofing”. They blame the company name they see in the inbox.
Once trust is lost, it is very difficult to rebuild.
What Is SPF and Why It Matters
SPF (Sender Policy Framework) is the first line of defence for your domain. It tells receiving mail servers which systems are allowed to send email on behalf of your domain.
How SPF Works
SPF uses a DNS record that lists authorised mail servers. When an email is received, the recipient’s mail server checks the SPF record. If the sending server is not listed, the email can be flagged or rejected.
Why SPF Is Important
Without SPF:
- Anyone can send email pretending to be your domain
- Your domain can be abused in spam campaigns
- Legitimate emails may end up in spam folders
With SPF configured correctly:
- Only approved servers can send email
- Spoofed emails are easier to detect
- Email deliverability improves
Common SPF Mistakes
Many businesses technically “have SPF” but still get it wrong:
- Too many senders added without review
- Incorrect syntax causing SPF failures
- Missing third-party services like CRMs or ticketing systems
SPF needs to be accurate and maintained as your email systems change.
What Is DKIM and Why It Matters
DKIM (DomainKeys Identified Mail) focuses on message integrity. It ensures that an email has not been altered in transit and that it genuinely came from the stated domain.
How DKIM Works
When an email is sent, it is digitally signed using a private key. The recipient’s server checks this signature against a public key published in DNS. If the signature matches, the email is verified.
Why DKIM Is Important
DKIM protects against:
- Email tampering
- Content modification by attackers
- Forged headers and sender details
It also improves trust with major email providers like Microsoft and Google, who heavily rely on DKIM when deciding whether to deliver or block messages.
Real Business Impact
Without DKIM:
- Emails are more likely to be flagged as suspicious
- Important messages may never reach customers
- Your domain reputation suffers over time
DKIM is especially critical for businesses sending invoices, password resets or automated notifications.
What Is DMARC and Why It Matters Most
DMARC (Domain-based Message Authentication, Reporting and Conformance) ties SPF and DKIM together and tells the world how to handle failures.
If SPF and DKIM are the locks on the door, DMARC is the security policy that says what happens when someone tries to break in.
How DMARC Works
DMARC checks:
- Does SPF pass?
- Does DKIM pass?
- Do they align with the visible “From” address?
Based on your DMARC policy, the receiving server will:
- Allow the email
- Quarantine it
- Reject it entirely
DMARC Reporting
One of the most powerful features of DMARC is reporting. You receive reports showing:
- Who is sending email on behalf of your domain
- Which emails pass or fail authentication
- Potential abuse or misconfigurations
This visibility is invaluable for ongoing security.
Why Using Only One Is Not Enough
A common misconception is that SPF or DKIM alone is sufficient. It is not.
- SPF can fail due to forwarding
- DKIM alone does not enforce policy
- Without DMARC, failures are often ignored
When all three are configured together:
- Spoofed emails are blocked before reaching inboxes
- Your domain reputation is protected
- Email delivery becomes more reliable
Major email providers now expect DMARC to be in place. Domains without it are increasingly treated as untrustworthy.
The Business Risks of Not Implementing DMARC, DKIM and SPF
Failing to protect your domain has serious consequences:
Financial Loss
Email fraud frequently targets finance departments. A single spoofed email can result in large unauthorised transfers.
Brand Damage
Customers receiving scam emails in your name will associate the problem with your business, not the attacker.
Deliverability Issues
Your legitimate emails may end up in spam or be blocked entirely, affecting sales, support and communication.
Compliance and Liability
Many industries now expect reasonable email security controls. Lack of protection can become a legal or contractual issue.
Common Misconception: “We Are Too Small to Be Targeted”
Attackers do not manually pick victims one by one. They use automated tools that scan the internet for unprotected domains.
Small and medium-sized businesses are often targeted more frequently because:
- They are less likely to have protections in place
- Staff may have less security training
- Email domains are easier to exploit
Size offers no protection. Configuration does.
Implementing DMARC the Right Way
A proper rollout matters. Moving straight to a “reject” policy without analysis can break legitimate email flows.
A sensible approach includes:
- Auditing all email sources
- Fixing SPF and DKIM alignment
- Starting DMARC in monitoring mode
- Reviewing reports
- Gradually enforcing quarantine and reject policies
This process protects your domain without disrupting business operations.
How CK Computer Solutions Can Help
Protecting your email domain is not just about adding a few DNS records. It requires understanding your full email ecosystem, monitoring reports, and maintaining configurations as your business evolves.
CK Computer Solutions – Managed IT Services Dublin works with businesses across Ireland to secure email domains properly and permanently. As a managed service provider, we can:
- Audit your existing email setup
- Correct and optimise SPF, DKIM and DMARC records
- Safely implement DMARC enforcement
- Monitor ongoing reports for abuse or misconfiguration
- Integrate protection across Microsoft 365, Google Workspace and third-party platforms
- Provide ongoing managed support as part of your IT services
By outsourcing this to a trusted MSP, you reduce risk, improve email deliverability, and protect your brand from abuse — without adding complexity for your internal team.
If your domain is not fully protected, or if you are unsure whether your current setup is correct, CK Computer Solutions can put the right controls in place and keep them working as your business grows.