We’re all guilty of quickly skimming through emails, especially on a Monday morning or just before clocking off. That’s exactly what cybercriminals are banking on. One of the more subtle phishing tactics doing the rounds lately is the “Task List” phishing email — a seemingly harmless message that pretends to help you stay productive, while quietly compromising your data or systems.
Let’s unpack what this scam looks like, how it works, and what your team can do to avoid falling victim.
What Is a “Task List” Phishing Email?
A “Task List” phishing email is a cleverly disguised message designed to look like a shared task update, project assignment, or a to-do list from a colleague or manager. It typically includes:
- A subject line like:
“Please see your updated tasks”
“Tasks assigned to you this week”
“[Project Name] Task List – Urgent” - A body that sounds generic but urgent:
“Hi, please review the tasks assigned to you and mark what’s completed.” - A link to a malicious site, often masked as a Microsoft 365, Google Docs, or Trello board.
- Sometimes a PDF, Excel, or even SVG file attached as a “task list”.
The moment you click the link or open the attachment? You’ve either been tricked into entering your login credentials, or malware has begun installing in the background.
Why This Works So Well
The brilliance (and danger) of the task list phishing email lies in its familiarity and timing. We’re all used to getting these kinds of emails, especially in hybrid or remote workplaces where teams rely on tools like Microsoft Teams, Monday.com, Asana, and Slack.
It taps into:
- Routine – Most people won’t question an email titled “New Tasks Assigned”.
- Hierarchy – When it looks like it’s from your boss or department head, you’re more likely to act.
- Time pressure – Words like “urgent”, “overdue”, or “needs review today” add a false sense of urgency.
- Imitation – Many phishing emails mimic real platforms (Microsoft 365, Notion, ClickUp) so they pass the visual sniff test.
Even an SVG Attachment Could Be a Trap
One of the more sneaky tricks in task list phishing emails is the use of SVG (Scalable Vector Graphics) attachments. These files look like harmless icons or images but can be embedded with dangerous code.
Unlike static image formats like JPG or PNG, SVG files are XML-based, meaning they can:
- Contain clickable areas that redirect to phishing websites
- Embed fake login forms designed to mimic Microsoft or Google portals
- Launch JavaScript or HTML-based payloads when opened in a browser
Because most devices open .svg files in a browser by default, the attack can bypass email filters and trigger immediately — no need for the user to “enable macros” or download anything extra.
If you receive a file named something like TaskList.svg, Tasks_Review.svg, or Q3_Todo.svg, it should raise a red flag — especially if you weren’t expecting one.
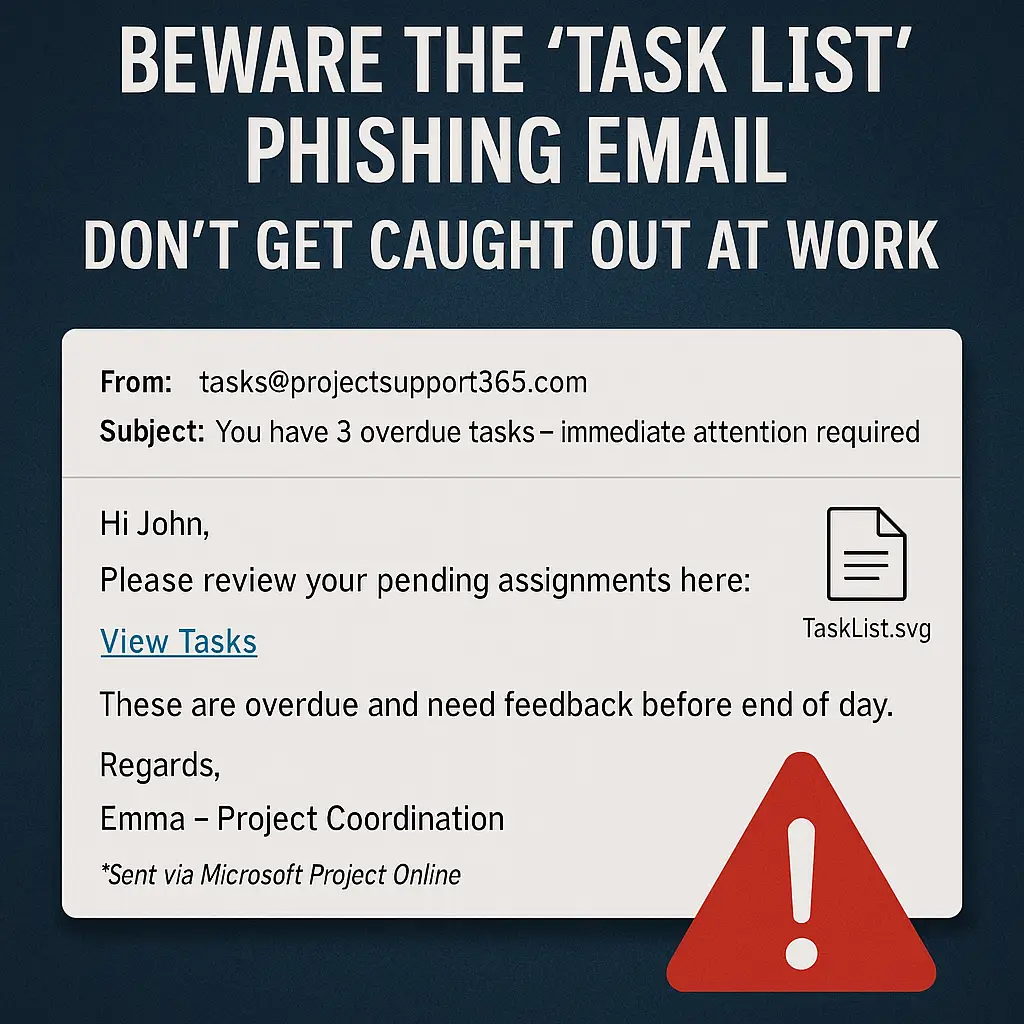
Real-World Example
Here’s how one might look:
From: tasks@projectsupport365.com
Subject: You have 3 overdue tasks – immediate attention requiredHi [First Name],
Please review your pending assignments here: [View Tasks]
These are overdue and need feedback before end of day.
Regards,
Emma – Project CoordinationSent via Microsoft Project Online
That [View Tasks] link might take you to a convincing Microsoft login screen — only it’s not Microsoft at all. It could be harvesting your credentials or redirecting you to a site where the SVG file runs malicious code in the background.
The Consequences of Falling for It
Clicking into one of these emails can unleash a chain reaction:
- Credential theft – Login details are stolen and used to breach your email, cloud storage, or internal portals.
- Business email compromise (BEC) – Attackers impersonate you to trick colleagues or customers into sending money or data.
- Malware infection – Downloads that seem like spreadsheets or task templates could infect systems with ransomware or keyloggers.
- Data loss or GDPR violation – Especially critical if client info, payroll, or contracts are compromised.
- Downtime and financial loss – Recovery from a phishing attack can cost small businesses thousands in downtime, IT recovery, and potential fines.
How to Spot a Phishing “Task List” Email
Even the best of us can be fooled, but here are signs to look out for:
- Unusual sender address – Looks close to a real address, but slightly off (e.g.
@m1crosoftonline.cominstead of@microsoft.com). - Generic language – “Dear colleague” or “Hi team member” with no personalisation.
- Unexpected task emails – Especially if you don’t normally receive tasks this way.
- Urgent tone – Tries to rush you into acting quickly.
- Dodgy links – Hover over links before clicking. Do they go where they claim to?
- SVG or other suspicious file types – If you weren’t expecting an attachment, don’t open it.
Practical Steps to Keep Your Business Safe
Here’s how to stop task list phishing emails in their tracks:
1. Train Your Team
Run phishing simulations or awareness sessions. Make sure staff know how to inspect emails carefully and report anything suspicious.
2. Use Multi-Factor Authentication (MFA)
Even if a password is compromised, MFA makes it harder for attackers to break in.
3. Lock Down Admin Access
Only give admin rights to staff who absolutely need it. Compromised accounts with admin privileges can do far more damage.
4. Use Email Filtering Tools
Configure Microsoft 365 or Google Workspace to filter out known phishing threats. Advanced threat protection is worth the extra few euro.
5. Implement Endpoint Protection
Modern antivirus or EDR (endpoint detection and response) software can catch dodgy attachments or links before they cause harm.
6. Verify Internally
If in doubt, double-check. A quick Teams message or call to your manager asking “Did you mean to send this task list?” can save a lot of grief.
How CK Computer Solutions Can Help
At CK Computer Solutions – Managed IT Services Dublin, we don’t just patch your PCs and walk away. As your trusted Managed Service Provider (MSP), we help protect your business from exactly these kinds of phishing scams.
Whether you’re a small team or a growing company, we offer:
- Phishing awareness training tailored to your staff and industry
- Email threat monitoring and filtering for Microsoft 365 and Google Workspace
- Setup and enforcement of MFA and secure logins
- Rapid response if something goes wrong – malware infection, account compromise, or suspected phishing
- Regular security reviews and best practice IT policies to stop problems before they start
If you’ve ever had that gut feeling about an odd-looking email or want peace of mind that your team won’t get caught off guard, we’re here to help.
Talk to CK Computer Solutions today to secure your business, train your staff, and keep phishing threats out of your inbox.